
The purpose of the Private Endpoints is to provide secure connectivity to Azure Storage from an Azure Virtual Network (VNet), by means of Azure Private Link. As of this month, this feature is generally available in all Azure public regions.
More info: https://azure.microsoft.com/en-us/updates/private-endpoints-for-azure-storage/
What is Private Link?
The purpose of this Azure service is to enable closed and secure access to specific Platform service (PaaS) and Azure/On-premises owned service tough private virtual network via a Private endpoint.
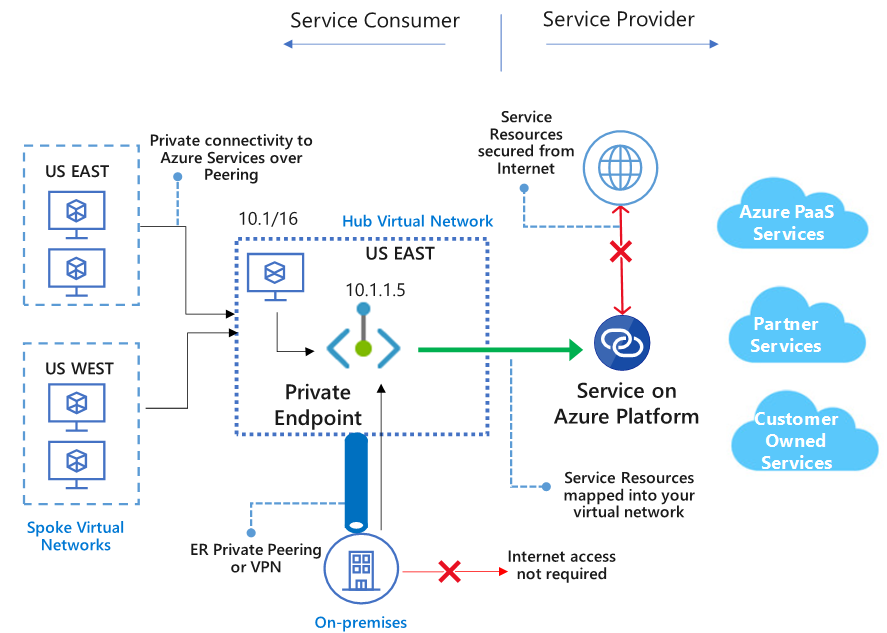
The traffic between the endpoint and the service will use Microsoft backbone network. this renders exposing Your service via a public interface, no longer necessary. The services offers SLA of 99.99%, and it comes with a price.
Key benefits
Azure Private Link, enables the following benefits:
- Privately access services on the Azure platform
- Privately access On-premises and peered networks
- Protection against data leakage
- Extension of Your own services globally
- Logging and monitoring (by integrating with Azure Monitor)
What is Private Endpoint?
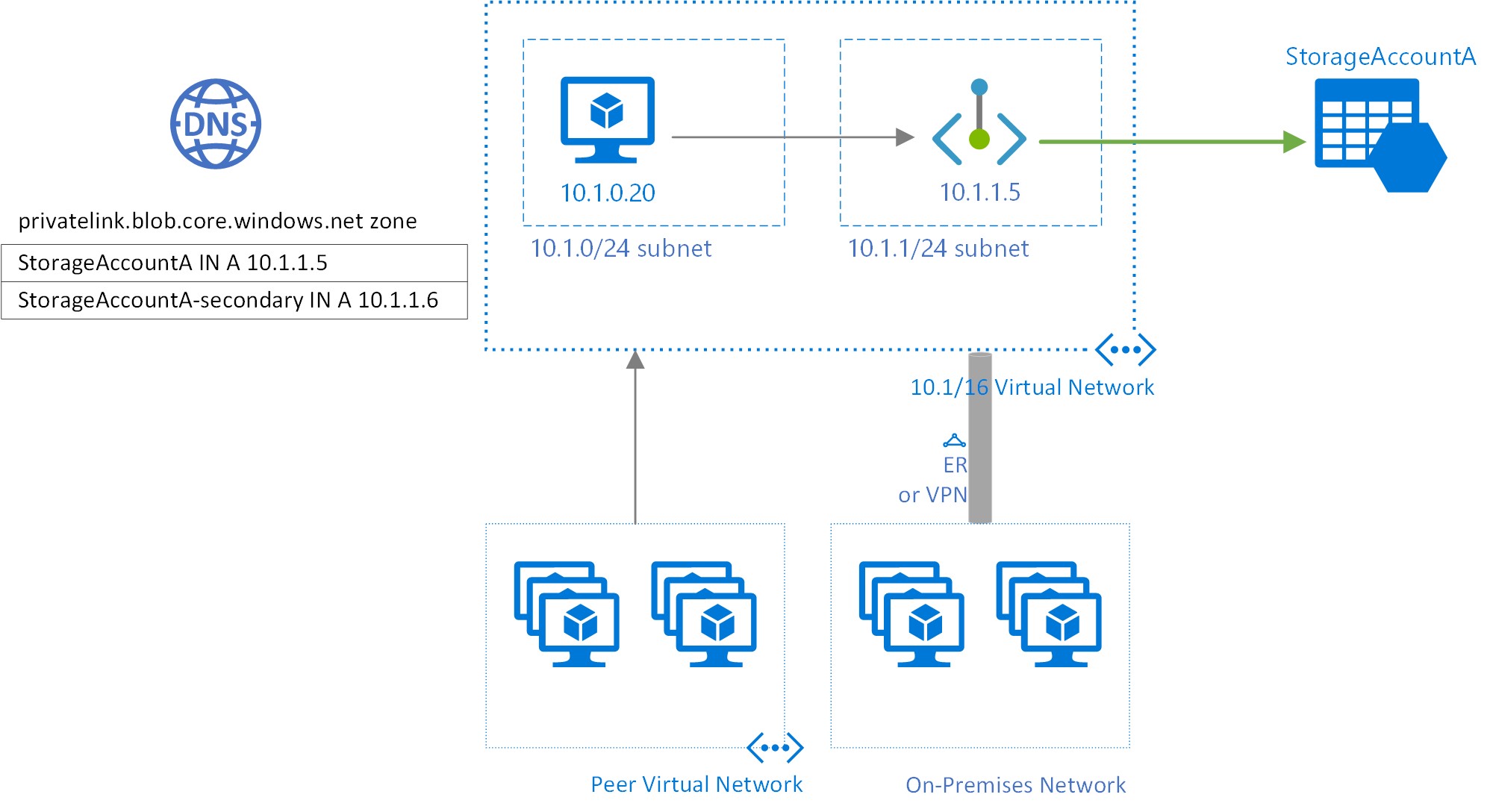
This is a network interface that connects you privately and securely to a service powered by Azure Private Link. The interface will use an IP address from Your private virtual network. The resources connected can be, as mentioned above Azure Storage, but also – Azure SQL Database, Azure Cosmos Database, Azure Database for PostgeSQL, MariaDB or MySQL.
Key features
Some of the features of the Private Endpoint are:
- Private connectivity can be established between resources in same VNet, Regional or Global Peered VNets and on-premises by using VPN or ExpressRoute, trough the Private Link service
- The Private Endpoint must be deployed in same region as the VNet
- The Private Link service can be deployed in different region than the Private Endpoint and VNet
- Single Private Ling service can be assigned to multiple Private Endpoints.
- Multiple Private Endpoints can be created within a single or multiple subnets, within a VNet
- Traffic is secured, by performing access control to validate the connectivity to a resource. there is a specific approval workflow, based on your RBAC settings, that will automatically allow access. In case the account is not authorized, an manual approval process can be initiated (Request access)



Be the first to comment