
In Part 1, of the series, we set the stage for Cloud Adoption Framework, focusing on Strategy. After that, in Part 2, we talked about Plan Phase and its major components and activities. However, we still have ground to cover, especially in the Adopt Phase. In conclusion, lets focus on the quick win areas, from the technical standpoint.
If You missed the previous two parts, refer to the links bellow
Cloud adoption in the era of accelerated Digital Transformation –
Part 1 and Part 2.

In this article, we will focus on the Ready Phase, specifically around the team Azure readiness, and map some quick win projects that will evolve around Governance, Security, and Management, as well as specific First workloads.
Governance and Security
Usually, there is tension between innovation and security/identity strategies. Business innovation, encompasses transformation, modernization, improving efficiency, driving costs down. On the other hand, security and/or identity strategies look at the security risks, that might emerge from the business innovation process – data loss, downtime, breach, malware attacks.
We also need to understand that, introducing the Cloud within our environment (hybrid model), means that the security is partnership between the cloud provider (Microsoft) and us. On one hand, we have Microsoft, which builds its cloud services on foundation of trust and security. The platform embeds security controls and capabilities that help us protect our data and application (services)
More information can be found at the Azure Trust Center: https://www.microsoft.com/en-ww/trust-center
On the other side, we own the data and identities, as well as the responsibility for protecting them. We own the security of on-premises resources, and all cloud components we. The first thing to understand about cloud security is that different scopes of responsibility exist, depending on the kinds of services you use.
For example, if you use virtual machines (VMs) in Azure, which provide Infrastructure as a Service (IaaS), Microsoft will be responsible for helping secure the physical network, physical storage, and virtualization platform, which includes updating the virtualization hosts. But we will need to take care of helping secure your virtual network and public endpoints and updating the guest operating system (OS) of the VMs.
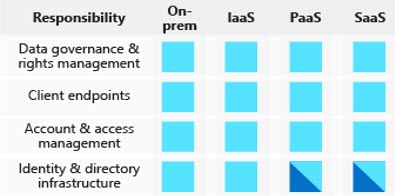
Regardless of the deployment type, you always retain responsibility for the following:
- Data
- Endpoints
- Accounts
- Access management
We share responsibility in the PaaS and SaaS model, for the Identity and Directory Infrastructure.
As far as the whole Governance and Security model goes, the underlying services we can utilize are:
- Azure Active Directory: Cloud based directory and identity management
- Resource Manager: Organize, deploy, and control resources in Azure
- Policy and Blueprints
- Azure Security Center: Prevent, detect, and respond to threats with increased visibility
- Azure Monitor: Collect, search, and visualize machine data from on-premises and cloud
Our control plane for identity is Azure Active Directory. From creating a centralized user and group management structure, for organizations that do not have such infrastructure deployed on-premises (one of the pre-requisites is to have Windows 10 on the endpoints). For organizations that already have established on-premises Active Directory structure, synchronization will be done by AD Connect tool, as well as extended features can be obtained by upgrading from Azure Active Directory Free to Basic or Premium subscription.
Quick wins: Azure Active Directory
– Simplify access and control of both Cloud and on-premises applications
– Rapidly develop and deploy new enterprise functionalities (Conditional Access, Multi-Factor Authentication, Rights Management)
– Utilize Self-service capabilities
– Utilize build-in reporting and logging capabilities
– Fail-safe: Azure AD Directory Services
Azure Connectivity
Any form of integration between on-premises systems and the cloud, would not be possible without the network connectivity. Azure Virtual Networks represent an logical network boundary, that provides:
- Automatic, but customizable routing (System, BGP or User Defined Routes)
- Built-in, but customizable DNS name resolution (Private/Public DNS service)
- Support for TCP, UDP, and ICMP
- Divided into one or more IP subnets (CIDR addresses, IPv4 or IPv6)
- Built in security features (Network Security Groups, Service Endpoints)
The cross-virtual network connectivity (in Azure) is done by means of peering, and for connectivity with external systems (on-premises, endpoints, 3rd party datacenters) an VPM (Site-to-Site; Point-to-Site) or Express Route can be used.
Additional Azure based or 3rd party appliances can be used for additional security, traffic routing, protection, such as: Azure Firewall, Load Balancer, Traffic Manager, Application Gateway, Front Door services, Network Virtual Appliances (Marketplace or Custom Images deployed)
Quick Wins: Azure Connectivity
– Hybrid connectivity capabilities and extension of on-premises networks
– NVA re-use/integration (Cisco, CheckPoint, PaloAlto, Sophos, Open Source …)
– Embedded monitoring capabilities
– Maintain Network Design/Architecture and Security Models
Infrastructure as a Service (IaaS)
With the underlying network services, and supported by the Governance and Security services (as stated in above sections), we can integrate our on premises datacenter infrastructure with the Azure one without compromising our already established policy and governance models, security posture, and available services/applications for our users.
For proper mapping of what we can use in Azure, we would need to run some of the available tools for that process, as well as use services that will enable the Lift & Shift (or as Greggor Suttie put it once: Move & Improve) of critical workloads that we can expose to external users. We discussed this in Part 2 of the series.
This will enable us to choose the appropriate VM size for our IaaS workloads. If we are under time pressure and we can’t perform deep analysis, we can optout to generalizing the used VM size for all workloads (4 vCPU, 8Gb RAM), and then use embedded services, like Azure Advisor and/or Azure Monitor, to optimize the VM’s operations, availability, and cost.
The deployments we are looking at are:
- Virtual Machines
- Minimal learning curve for existing virtualization professionals
- Run most Windows or Linux-based workloads (Supported, or Custom images)
- Easiest target for migrating to the cloud (Azure Migrate + Azure Site Recovery)
- Flexible instance sizes – use the best fit for your workload (General Purpose, Compute Optimized, Memory Optimized, etc)
- Automation, Security, Integration, Hybrid network capabilities
- Virtual Machine Scale Sets
- All the power and flexibility of a Virtual Machine
- Designed for high-end workloads
- Automatically scale up (or down) to 1000 instances
Depending on the options selected, we can improve our IaaS resiliency and availability significantly.
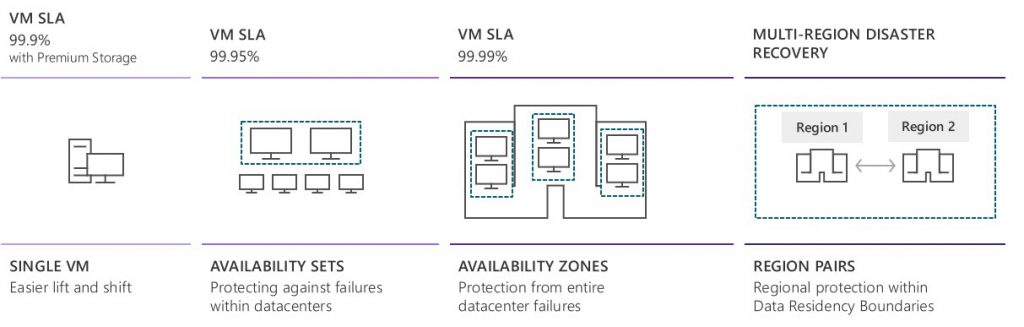
Quick Wins: Virtual Machines
-Focus on Move&Improve workloads (Lift&Shift)
– Public facing services (i.e. Web sites, Web services, eCommerce)
– Start small, then automate scaling (Out and In)
-Use Azure platform monitoring capabilities
Remote Desktop Services
I see quite a few organizations, where with their traditional business model, most of their workers have static devices (PC’s), and up till now, were never considered as Work-From-Home type of users. Recent development, proved that this is not sustainable model.
In Azure, you can go fore two models, to enable remote access to services/applications for the employees:
- Remote Desktop Services
- Windows Virtual Desktop
Remote Desktop Services (RDS) is the platform of choice to cost-effectively host Windows desktops and applications. You can use an Azure Marketplace offering or a QuickStart template to quickly create an RDS on Azure IaaS deployment.
Difference being is, that marketplace deployment creates a test domain for you, making it a simple and easy mechanism for testing and proof-of-concepts. With the QuickStart templates, you can use an existing domain, which will be the easiest way to deploy the service and integrate it with Your infrastructure. The QuickStart templates can be found on the following location.
On the other hand, Windows Virtual Desktop (WVD) is managed service, that runs on the cloud. The Microsoft managed portion of it, besides the infrastructure (compute, storage), handles the Web Access, Diagnostics, Gateway, Management, Broker and Load Balancing of the desktop service. We control the OS deployed and Remote Applications installed. The services is regularly updated with new features and capabilities, so make sure You visit the WVD documentation site
Quick Wins: Virtual Desktop
– Enable secure and managed access to Corporate Applications and Services
– Create fully managed desktop virtualization environment
– Run multiple host-pool for different purposes
– Use it till You need it
Conclusion
It took us some time, to get to the end of my 2 cents on the accelerated Digital Transformation we are facing in the past few months. I felt that going trough the Cloud Adoption Framework is a valuable step, before we get to some of the so called, Quick Wins.
From my experience, these look like feasible and realistic projects we can run in Your organizations or propose them to Your clients.
What we discussed in this 3-part series, will provide a ground for potential, further integration, and cloud adoption. Integration with third party services and applications, introducing Microsoft/Office 365, amending existing Security, Monitoring and Governance tools. On the other hand, this might be a completely new journey You can undertake in the cloud.
We did not have a chance to focus on the training and readiness component, but for that, at time being look at Microsoft Learn, edX , PluralSight, local training center or freelance trainer that can work with You, and build a customized training roadmap for Your teams
Comments or opinions are welcome, and till then stay safe and keep (digitally) transforming!




Be the first to comment