
Introduction
As it turns out migrating your infrastructure to Azure is more than simply re-hosting your applications. It’s an opportunity to transform the way the organization operates by leveraging cloud-native capabilities. Furthermore, its a set of patterns and anti-patterns during migration to Azure.
Drawing from multiple migration projects, I will try to convene some “lessons learned”, some “Aha!”, “Doh!” moments from the process. I will probably need more “paper” for this article to convene everything. (I feel that it’s moving towards an actual event session, as we speak) ?
In this article, we explore both the effective strategies (patterns) and the common pitfalls (anti-patterns) encountered during an Azure migration journey. Furthermore, when identifying these “red flags” early in the process, organizations can avoid costly missteps and ensure a smoother, more efficient transition to the cloud.
Laying the Groundwork for Migration
So, where do we start? This is the time I always refer to my old friends – Cloud Adoption Framework (CAF), Well-Architected Framework (WAF), and Azure subscription and service limits, quotas, and constraints. That’s where all the fun is. This is the way to Cloud adoption Plan!
Note:
I always talk about the above, and some more …. Check out some of the previous articles, related to them, in the Azure section.
Now, we can debate for a long time on this topic. But, let’s set some grounding first. Ultimately, for any process of embarking on Cloud journey, we need to do a proper preparation and assessment.
Begin by inventorying your existing infrastructure and applications. Understand dependencies, performance baselines, and security needs. Then, consider which migration strategies fit best:
- Lift-and-Shift (Re-hosting): This produces quick results, but it comes with baggage.
- Re-platforming: Requires no or minimal changes to the applications, and a step towards true cloud-native applications.
- Refactoring/Re-architecture: At this point, you go back to the ‘drawing board’, and go for the cloud-native application/service environment.
- Hybrid: Kind of ‘best of both worlds’ scenario. There might be various reasons, but it is a rather common approach..

Remember, we start with identifying key objectives for migration to Azure (e.g., cost savings, scalability, improved performance) and ensure that technical decisions align with business goals. Always keep detailed documentation of the current state. Inadequate documentation is a red flag that could lead to unforeseen challenges later. Hence, we follow the patterns, and identify the anti-patterns.
Patterns for Migration
Having all of the above in mind, what constitutes as effective patterns in this process? In all fairness, there might be quite a lot, but I will focus on just a few that I have experienced.
Phased and Iterative Migration
Rather than a Big-Bang approach, break the migration into manageable phases. Frankly, the Big-Bang approach was much more on the table, than I would have liked it to be. I see the tendency of doing everything in “one-shot” in small/mid-size organizations. All in all, its related to cost-time rations, but in other is to the experiences and knowledge on the teams. Meaning, they know their current environment and the feeling is that Azure is the same. And, this is the problem that causes migration failures, delays, and increased cost-time ratios. Hey, ultimately this can lead to success or failure of the migration process itself.
Security by Design
Implement strong security measures from the outset. I always reference this as Security baseline. It’s not just something that used to be (on-premises), it is enhancing it with built-in capabilities of the Azure services. Furthermore, it’s related to the migration strategy chosen in the begging. The more we are leaning towards cloud-native, the we rely on built-in security principles and models. For everything else, we have the Well-Architected Framework, and Microsoft Cybersecurity Reference Architectures (MCRA). Early signs of breaches or non-compliance should prompt immediate review of security practices.
Resilience and Scalability
Design for fault tolerance by leveraging availability zones, load balancers, and disaster recovery planning. These enhancements come with the built-in capabilities of Azure services. It helps organizations improve operations and embed these capabilities within their application portfolio. Sounds easy enough, but these are important design decisions that are made at the begging. For some of them, like availability zones, we need to be careful. For example, if we change our mind later in the project, that might imply re-deployment of the whole environment. At that point, phased approach really seems like a good idea.
Cost Management and Optimization
Monitoring spending is something that needs to be planned since the begging. From choosing the initial operation model, to any design/architecture decision made it will affect it. It is our fail safe when there is something wrong – issues with architecture, scalability, resiliency, updates, attack on the services. A spike in costs post-migration may indicate inefficient resource use or misconfiguration. It is a never ending story, once you get your workloads in the cloud!
Monitoring and Logging
Pretty much all of the above items, as well as the one bellow are connected with this one. Implement robust monitoring using Azure Monitor and Application Insights to track performance, detect anomalies, and optimize resource usage. Inconsistent performance metrics or unexplained downtime can signal that the migration strategy requires reevaluation.
Anti-patterns for Migration
Unfortunately, there is no web page or a “big book” outlining the anti-patterns. It’s something that becomes obvious, during the embarked cloud journey process. It is a natural occurrence, between the stakeholders – Business and IT Operations teams. They can appear in different phases of the adoption process (Plan, Ready, Manage, Govern, Organize).
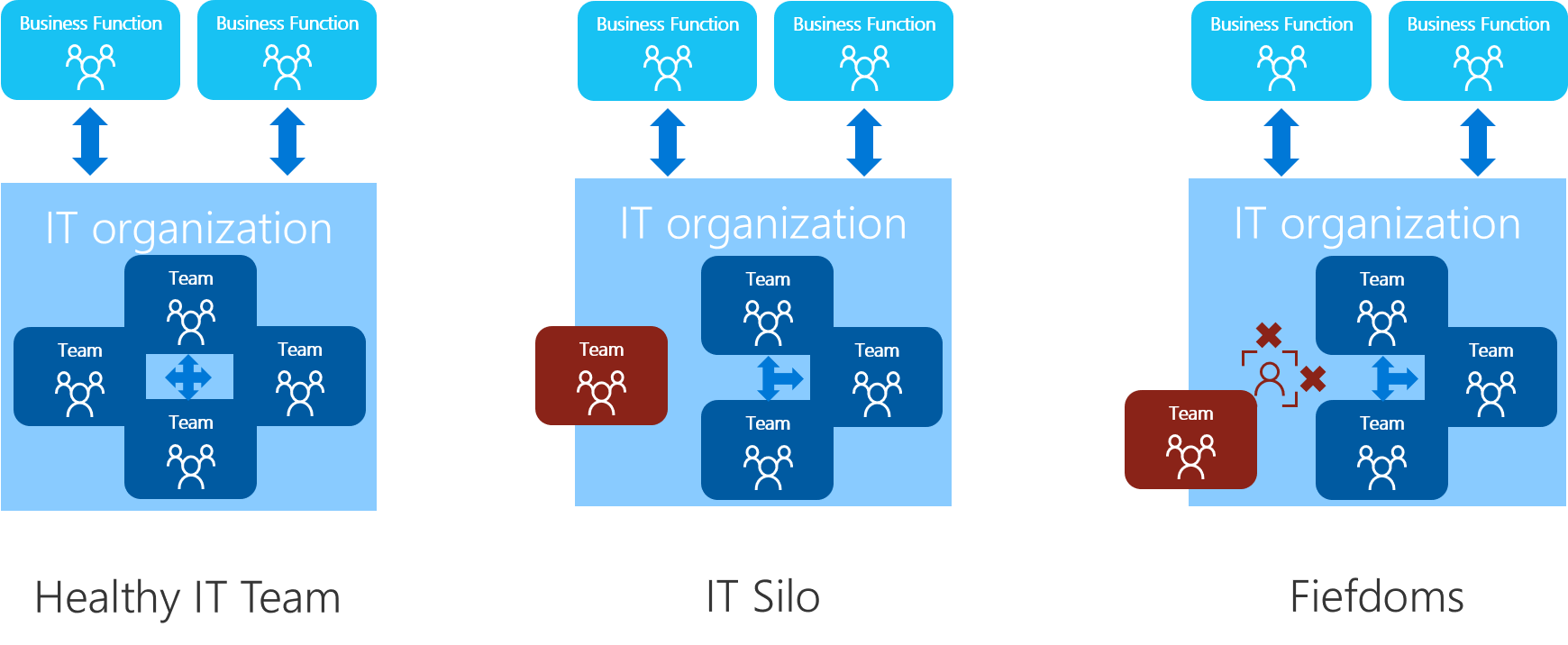
I’ve seen this happen ever before the begging of the project. As I always tell people, embarking on the Cloud Journey, is a disruptive process fore every organization. It’s not just connected to the size or the complexity of their environment. It affects the people as well, since it affect the organizational structure and alignment.

All things considered, we tend to keep within our so called comfort zones. And we are very territorial about that.
How fast and efficient are we in dealing with it, as an organization, depends on the alignment model chosen. Hence, the results might vary, as well as the timeline for achieving the goals.
In other words, let’s dig in into some of the anti-patterns I observed in various migrations to Azure.
Blind Lift-and-Shift
Migrating without revisiting the architecture can lock you into inefficiencies. Simply “lifting and shifting” legacy architectures might prevent you from capitalizing on cloud-native benefits like scalability and managed services. Likewise, it just brings old problems into the new environment.
Underestimating Complexity
Failing to account for inter-dependencies, regulatory constraints, or data gravity can derail timelines and budgets. A thorough initial assessment is key to understanding hidden complexities. Rationalization of your digital estate matters. If you notice undocumented dependencies or gaps in system documentation, it’s a red flag. These issues can lead to integration problems post-migration. Always remember, You are moving on-premises services to distributed and asynchronous environment!
Loose Security (or putting too much fate in the built in capabilities)
Identity management, encryption, and network segmentation need to be interwoven. Now, that might create security gaps. Look at already established models, architectures and/or recommendations for Azure. Never assume that you have figured everything out. Hybrid solutions brings benefits, but can also create gaps. The standards are there, there best practices as well (i.e. Well-Architected Framework – Security Pillar, Microsoft Cybersecurity Reference Architectures (MCRA)). Do not lower Your gard, just because there are built-in capabilities.
Ignoring Governance
Without proper policies and tagging strategies, you risk cloud sprawl, resource mismanagement, and unexpected costs. Establish a governance framework early in the migration. It’s the Governance baseline for everything that follows. Not establishing benchmarks before migration, can make it hard to measure success or pinpoint issues later.
Inadequate Testing and Validation
Rushing trough the migration phases without proper testing can lead to disruptions. Implement staged rollout, validate components in a production-like environment. Explore different environment design areas. After all, it is your conceptual architecture!
Poor Change Management
Ignoring the human side of migration, such as inadequate training, resistance to change or not knowing the technology enough. This can cause delays or impede progress of the cloud journey. Knowledge transfer and training is important. This gives a change to the subject matter experts (SMEs) to get to know the environment. In that way, they can support the process of design/architecture, and operations in the new environment. Catch 22: Not all organizations go trough the training before the start of the journey to the cloud.
Lack of Stakeholder Buy-In
Resistance from IT teams or key business units can be a red flag that the change management process needs more attention. It can be related to falling for the buzz words, miscommunication between stakeholders, poorly defined strategy, and/or fear of the unknown (comfort zone).
Recommendations
So what can we add, as things to be considered in this process? I will try to summarize then in just a few points, such as:
- Phased Approach: Break the process into phases. Try to establish clear milestones and think of feedback loops. This allows you to learn from Your mistakes (patterns, anti-patterns), and adjust as you progress.
- Rely on the Cloud-Native Capabilities: Instead of ‘playing it safe’ and just use on-premises setups, adapt to Azure’s native capabilities. This will enhance the IT Operations, in areas such as security, scalability, and performance.
- Continuous Learning (The never ending story): Again, we are talking about a very dynamic environment. Cloud services, capabilities and features are constantly changing. We need to keep up, as much as possible.
- Go Beyond organizational boundaries: Don’t expect that you will have all the necessary SMEs in the organization. Fill in the gaps by reaching out to experts, outside of the organization. This will help fill in the knowledge/expertise gaps, while Your team gets the hang of the new technology. No matter if it is short, mid or long term.
Useful links
Github repo with useful links: Migrating Infrastructure to Microsoft Azure using Cloud Adoption Framework (CAF)




Be the first to comment