
Just-In Time VM Access
This feature, that is found and configured within the Azure Security Center, is part of he Standard Pricing tier. In a nutshell, this feature enables lock down of Azure VM with just-in-time (JIT) access. This is a simple but effective way to reduce the attack surface on Your VM’s.
Attack vector
This feature handles so called “Brute Force” attacks, directed at management port of the VM’s. One way to block these attacks is reduce the exposure of the VM’s. Since management ports are not used all the time, we can create a specific configuration that will prevent attacks. At the same we will enable access to them, in timely manner.
In this case, these are (by default):
- SSH (Port 22) for Linux
- RDP (Port 3389) and WinRM (Port 5985, 5986) for Windows VM’s
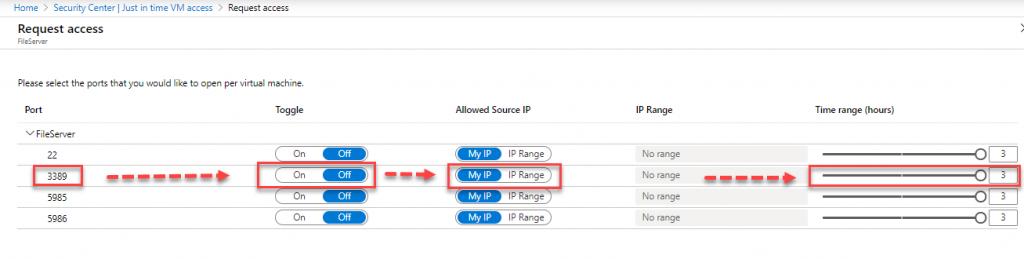
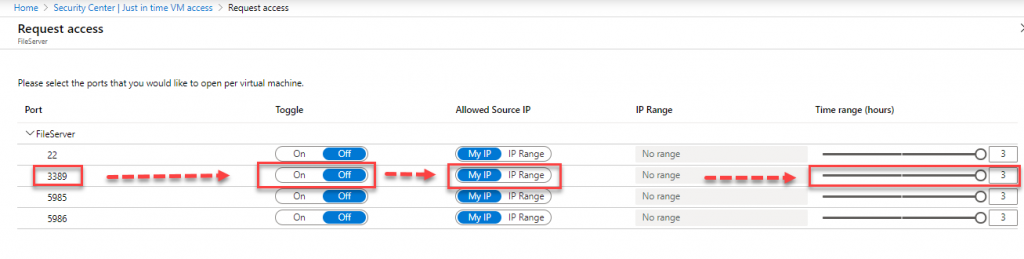
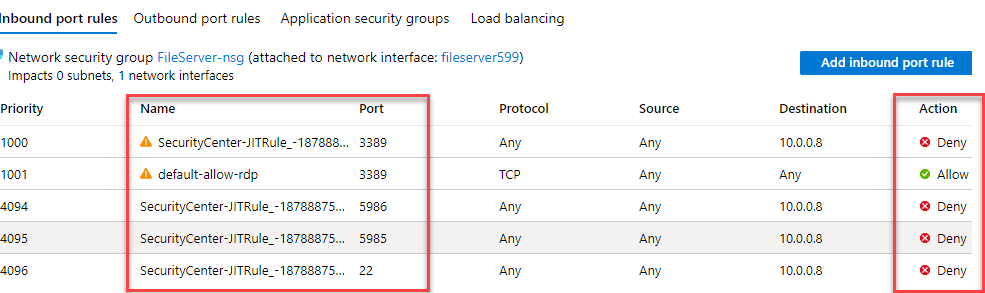
Once we enable this feature, trough Security Center, two things will happen:
- Specific Network Security Group (NSG) rules are created, for selected machines and ports, Allowed Source IP, Maximum Request Time.
- Each time a users asks for access to those ports, given that appropriate rights are given (RBAC), the request is approved
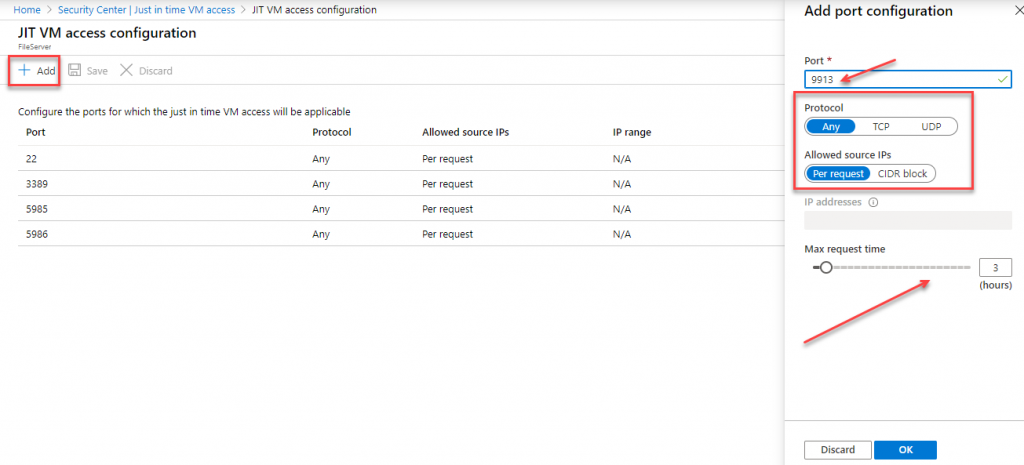
You can always add custom ports, depending on Your needs. For each port, You need to define Port Number, Protocol Type (All, TCP, UDP), Allowed Source IP (single or block, CIDR format), Maximum Request Time (between 1 – 24 hours, default is 3h)
Updates – March 2020
One of the new features added, is the Justification field – free test style entry field (optional). This information is in the logs, for audit purposes.

Another new update, is an governance feature, they also created a clean up tool. Every time the the JIT policy is changed/refreshed, the tool runs and checks the validity of the whole rule set. It compares the policy and the NSG rule, and if it finds mismatch, determines the cause and fixes the issue. It will do rule set cleanup.
This only works with built-in rules.



Be the first to comment