
The magic of automation: How to set up Conditional Access Policies without lifting a finger
These policies streamline identity protection, providing a more comprehensive security framework for users. Conditional Access presents a robust solution, but we do need guidance on creating and deploying policies that suit unique needs. Microsoft’s managed Conditional Access policies are here to meet those demands.
It was already announced on the Microsoft Security blog:
Automatic Conditional Access policies in Microsoft Entra streamline identity protection | Microsoft Security Blog
How it started
In the early days of cloud identity, implementing MFA was a complex process involving vendor selection, service configuration, and user persuasion. Microsoft later simplified this by making MFA the default for consumer accounts in 2013 and for enterprise accounts in 2019 with Security Defaults.
These basic controls included:
- Requiring all users to register for multifactor authentication
- Requiring administrators to do multifactor authentication
- Requiring users to do multifactor authentication when necessary
- Blocking legacy authentication protocols
- Protecting privileged activities like access to the Azure portal
This approach led to a significant reduction in account compromises, thanks to increased multi-factor authentication (MFA) usage. It did help, but requiring Administrators to use MFA, complicated the usage of emergency access account admins . We recommend excluding them from any MFA and/or Conditional Access policy. With Security Defaults, this was not possible.
It did provide security hardening of existing and/or future tenants, with free license for Microsoft Entra ID.
Conditional Access Policies provided finer control, and this functionality was exclusively available to users holding a Microsoft Entra ID Premium license.
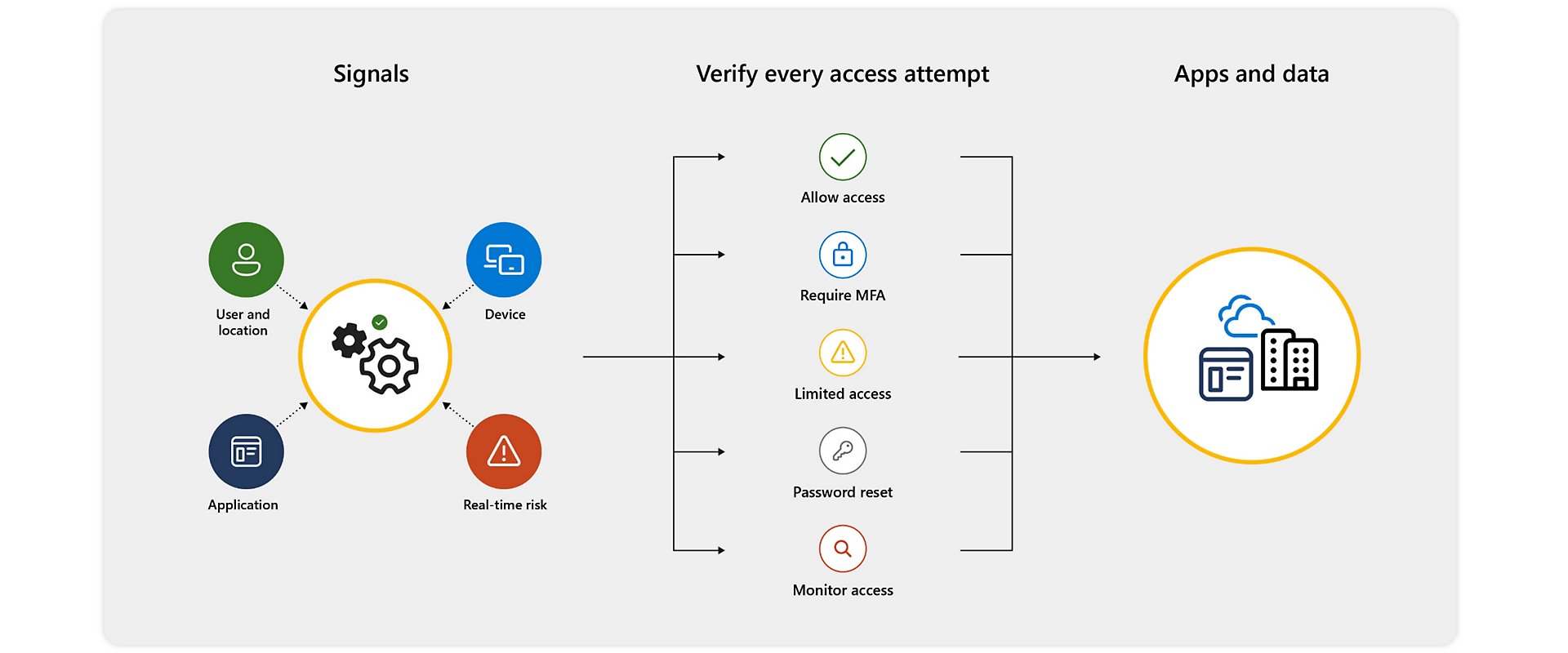
At its core, Conditional Access Policies are akin to basic if-then statements: when a user seeks access to a resource, a specific action becomes a prerequisite. For example, when a user wishes to access an application or service like Microsoft 365, they must complete MFA to secure their access.
How it is going
Now, the next step in this journey involves the automatic deployment of Microsoft-managed Conditional Access policies. These policies offer straightforward, self-deploying recommendations, allowing You to adjust or disable them as needed, making them accessible to organizations of all sizes and complexities. While tailored policies for specific organizations will become available over time, the initial focus is on simplicity. Given the importance of MFA for enhancing identity security, the first three policies reflect that, as outlined in the table below:
| Policy Name* | Aimed at | What it does |
|---|---|---|
| Require MFA for admin portals | All customers | This policy encompasses the high-and-mighty admin roles and mandates the use of MFA whenever an admin logs into a Microsoft admin portal. |
| Require MFA for per-user authentication | Existing per-user MFA customers | This policy is tailored for users equipped with per-user MFA, making it mandatory for all cloud applications. It facilitates organizations in their shift towards Conditional Access. |
| Require MFA for high-risk sign-ins | Microsoft Entra ID Premium Plan 2 customers | This policy extends to all users, necessitating both MFA and re-authentication during sign-ins deemed high-risk. |
The first policy introduces one very important change, since this feature was only available for Microsoft Entra ID Premium Plan 1 and 2. While opting out is possible, Microsoft will increasingly require MFA for specific interactions. They already do, for certain Microsoft 365 and Azure management scenarios, access to Partner Center, and Microsoft Intune device enrollment.

You can easily monitor these policies through the new policy view user interface, which offers a summary of the policy, alerts, recommended actions, and an impact summary. Customization options are available, allowing the exclusion of users, groups, or roles as exceptions, including emergency and break glass accounts. For more extensive customization’s, policy cloning is an option, enabling as many changes as needed.
What’s next
The gradual rollout of these policies to all eligible tenants will commence in mid-November, and advance notification will be provided. Upon visibility in Your tenants, you will have a 90-day window to review, customize, or disable these policies before they become active. During this period, the policies will operate in report-only mode, logging policy results without enforcing them.
Furthermore, these policies will continue to evolve, with the goal of integrating machine learning-based policy insights and recommendations with automated policy deployment.
Additional links
Microsoft Entra ID service description (formerly Azure Active Directory)
Common Conditional Access Policies
Microsoft Entra ID – Risk Detection




Be the first to comment