
If you are using Azure, you might wonder how to keep track and manage your resources effectively. In this blog post, I will share with you some insights and best practices on how to achieve visibility and control in your Azure environment. This is aimed at improving Azure operational efficiency for the services running.
There are few challenges that come hand-in-hand with the cloud technologies/services, such as:
- Rapid-Fire Pace of Data Collection: The constant influx of data can make it difficult to keep up with governance needs.
- Growth and Turnover of New Technologies: As new technologies emerge and old ones become obsolete, governance strategies must adapt.
- New Data Sources: The introduction of new data sources can complicate governance, as each source may require unique policies and procedures.
- Internal Friction: Differences in priorities or understanding between teams or departments can hinder effective governance.
- Evolving Enterprise Infrastructure: As the enterprise infrastructure changes, so too must the governance strategies.
In the context of Microsoft Azure, these challenges can manifest in several ways:
- Understanding New Paradigms: Cloud governance is an iterative process that requires a shift in thinking from traditional IT governance. The ability to delete and rebuild an entire virtual datacenter with a line of code necessitates a rethinking of traditional approaches.
- Policy Integration: The level of corporate policy integration between on-premises and the cloud varies depending on cloud governance maturity and the nature of the digital estate in the cloud.
- Tool Utilization: Azure provides tools and services like Azure Policy, Azure Blueprints, and Microsoft Defender for Cloud to enforce and automate your organization’s governance decisions. Understanding how to effectively use these tools is crucial.
Additional information:
I had a session on Azure Spring Clean event covering this topic as well. Link from the video can be found here.
The Pillars of Azure operational efficiency
Maintaining proper visibility and control on Your environment is a journey, and it falls within the following principles:
- Performance: helps us identify and troubleshoot issues, such as latency, errors, bottlenecks, etc.
- Security: helps us protect their cloud resources from cyberattacks, such as malware, ransomware, phishing, etc.
- Compliance: helps us comply with regulatory requirements and industry best practices, such as GDPR, HIPAA, PCI DSS, etc.
- Optimization: helps us optimize the cost and efficiency of their cloud resources.
To overcome these challenges, organizations can use the Microsoft Cloud Adoption Framework for Azure, which provides guidance on assessing existing policies, building an initial governance foundation, and iteratively adding governance tools. It’s also important to foster a culture of collaboration and continuous learning within the organization.
Additional information:
Cloud Adoption Framework for Azure was covered in previous article (3 parts)
But, in this article, we will cover three main areas:
- Sandbox is the process of creating isolated and temporary environments for testing, development or experimentation purposes. This allows you to try new features, configurations or services without affecting your production environment or incurring unnecessary costs
- Governance is the set of policies, processes and tools that help you define and enforce the rules and standards for your Azure environment. This helps you ensure compliance, security, quality and consistency across your resources.
- Resource optimization is the practice of using your Azure resources efficiently and cost-effectively. This helps you avoid waste, reduce costs and improve performance.
Azure offers several tools and techniques for above mentioned pillars. We will go trough each separately, so let’s get started!
Sandbox Azure Environments
If you are new to Azure or want to experiment with different Azure services and capabilities without affecting your production or development environments, you might want to create a sandbox environment. A sandbox is an isolated and controlled environment where you can test and learn without risking any unwanted changes or costs.
Option 1: Use the Azure Sandbox service architecture
One of the easiest ways to create a sandbox environment in Azure is to use the Azure Sandbox service architecture. This is a collection of interdependent cloud computing configurations for implementing common Azure services on a single subscription. You can deploy all the configurations or just the ones you need, and you can customize them according to your needs. The Azure Sandbox service provides a flexible and cost-effective sandbox environment for experimenting with Azure services and capabilities.

Additional information:
GitHub repository with deployment scripts (Terraform) and additional instructions can be found here
Some of the benefits of using the Azure Sandbox service are:
- You can deploy a fully provisioned sandbox environment with just a few clicks.
- You can access a variety of Azure services and capabilities, such as SQL Server on Azure Virtual Machines, Azure SQL Database, Azure Database for MySQL Flexible Server, Azure Virtual WAN and point-to-site VPN, and more.
- You can reduce costs by stopping or de-allocating virtual machines when not in use, or by skipping optional configurations that you don’t plan to use.
- You can integrate the sandbox environment with an Azure landing zone for governance and security best practices.
Option 2: Use the Cloud Adoption Framework landing zone sandbox environments
Another option for creating a sandbox environment in Azure is to use the Cloud Adoption Framework landing zone sandbox environments. These are isolated environments where you can conduct Proof Of Concepts (POC) with Azure resources in a controlled environment. Each sandbox has its own Azure subscription, and Azure policies control the subscription. The policies are applied at the sandbox management group level, and the management group inherits policies from the hierarchy above it. Depending on its purpose, an individual or a team can use a sandbox.

Some of the benefits of using the Cloud Adoption Framework landing zone sandbox environments are:
- You can create multiple sandboxes for different purposes and projects.
- You can apply governance and security policies to your sandboxes at the management group level.
- You can track costs and cancel sandboxes when budgets decrease or when the sandbox expires.
- You can keep the sandbox isolated from your private network by denying network peering and gateway creation.
- You can enable audit logging for your sandbox environment for security purposes.
Additional information:
The reference architectures can be found here. They can be combined with the Sandbox environment guidance, mentioned above, for additional customization.
Governance in Azure Environments
This represents the process of ensuring that your cloud resources are compliant with your organization’s standards, policies, and regulations. Governance helps you manage costs, security, performance, and quality of your cloud services. There are several options for implementing governance in Azure environments, depending on your needs and preferences.
Azure Policy
This is a service that allows you to create and assign policies to your Azure resources. Policies are rules that define what actions are allowed or denied on your resources. For example, you can use policies to enforce naming conventions, restrict locations, limit SKUs, or audit configurations.
You can apply policies at different levels of granularity, such as management groups, subscriptions, resource groups, or individual resources. You can also use policy initiatives to group multiple policies together for a specific scenario or compliance standard. Azure Policy integrates with other Azure services, such as Azure Monitor, Microsoft Defender for Cloud, and Azure Blueprints.
Azure Blueprints
This is a service that helps you create and deploy compliant environments in Azure. Blueprints are packages of artifacts that define a set of resources, policies, role assignments, and parameters for a specific scenario or purpose. For example, you can use blueprints to create a fully governed environment for a development team or a business unit. Blueprints are used to ensure compliance with external regulations, such as ISO-27001 or PCI-DSS.
You can create your own custom blueprints or use the built-in blueprints provided by Microsoft. You can also publish, update, and assign blueprints to your Subscriptions or Management Groups.
Microsoft Defender for Cloud
Defender for Cloud is a unified platform that provides comprehensive security for your cloud resources. IT spans across across identity, data, devices, apps, and infrastructure. Microsoft Defender for Cloud helps you protect your cloud workloads from threats, vulnerabilities, and misconfiguration.
It also helps you comply with regulatory standards and best practices by providing security recommendations and assessments. You can use Microsoft Defender to monitor and secure your Azure resources, as well as hybrid and multi-cloud environments.
Azure Deployment Environments
This is a service that helps you create and manage consistent and compliant environments in Azure. Deployment environments are collections of subscriptions that are configured for a specific type of environment. This includes sandbox, testing, staging, or production environments. Azure governance is applied to those subscriptions based on the type of environment.
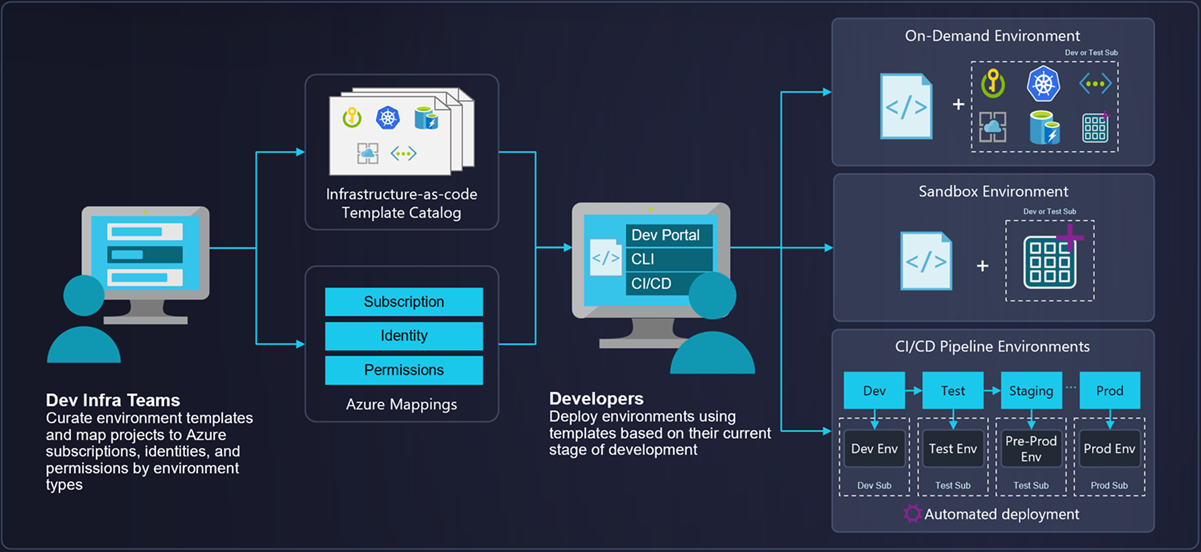
With Azure Deployment Environments, your platform engineer can enforce enterprise security policies and provide a curated set of predefined infrastructure as code (IaC) templates. Your developers can then use those templates to provision their own environments without compromising compliance or quality.
Resource Optimization in Azure Environments
If you are using Azure to run your workloads, you might be wondering how to optimize your environment for cost, performance, availability, and security. Azure offers many tools and services that can help you achieve your optimization goals, but it can be challenging to know where to start and what to prioritize.
Let’s explore some of the options for resource optimization in Azure environments, provide some additional details and useful links per option, and share some best practices and tips.
Option 1: Shut down unused resources
One of the easiest ways to optimize your Azure environment is to shut down or delete any resources that are not in use or needed. This can help you avoid paying for unnecessary capacity and reduce clutter in your environment.
You can use Azure Advisor, a free service that provides personalized recommendations for optimizing your resources, to identify idle or unused resources such as virtual machines (VMs), ExpressRoute circuits, VPN gateways, and more.
You can also set up alerts and budgets in Azure Cost Management and Billing to monitor your spending and usage patterns and get notified when you exceed your thresholds.
Option 2: Right-size underused resources
Another way to optimize your Azure environment is to right-size your resources based on their utilization and performance requirements. This means adjusting the size or configuration of your resources to match their actual needs, rather than over-provisioning or under-provisioning them. For example, you can resize your VMs to use a smaller or larger instance type, change the service tier and/or SKU of your database or storage account, or scale up or down your web app or function app. By right-sizing your resources, you can improve efficiency, performance, and cost savings.
Option 3: Use reserved instances and spot instances
Another option for optimizing your Azure environment is to use reserved instances and spot instances for your VMs. Reserved instances are pre-purchased VMs that offer significant discounts compared to pay-as-you-go pricing. You can reserve VMs for one or three years, and choose to pay upfront or monthly. Reserved instances are ideal for workloads that have predictable and consistent usage patterns, such as production or disaster recovery environments.
Spot instances are VMs that run on spare Azure capacity at a very low price, but can be evicted at any time. Spot instances are ideal for workloads that have flexible start and end times, such as batch processing, testing, or development environments.
These is a valid option in case You are running Infrastructure (IaaS) or mix of Infrastructure and Platform Services (IaaS + PaaS).
Option 4: Leverage Native Azure services and features
Another option for optimizing your Azure environment is to leverage the various services and features that Azure offers to help you reduce costs, improve performance, and enhance security. For example, you can use Azure Hybrid Benefit to reuse your existing Windows Server and SQL Server licenses on Azure VMs. Using different capabilities of Azure Storage Accounts to store your data in different tiers based on access frequency, such as hot, cool, or archive.
You can also use Defender for Cloud to protect your resources from threats and vulnerabilities, and Azure Monitor to collect and analyze metrics, logs, and alerts from your resources.
Additional links
I maintain a selection of blogs, articles, video content, related to Microsoft cloud technologies. It is refresh regularly. Please visit and bookmark the page if You are interested: GitHub Repository of Useful Links



Be the first to comment