
We are witnessing, that security architectures, that do not only rely on network firewalls and virtual private networks (VPNs) to isolate and restrict access to an organization’s technology resources and services. This proves to be no longer sufficient for a workforce that regularly requires access to applications and resources that exist beyond traditional corporate network boundaries.
As per Microsoft’s new guiding principles, we rely on Zero Trust security model. Its founding principles are:
- Verify explicitly
Always authenticate and authorize based on all available data points. This is where Zero Trust identity and device access policies are crucial to sign-in and ongoing validation. - Use least privilege access
Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection. - Assume breach
Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
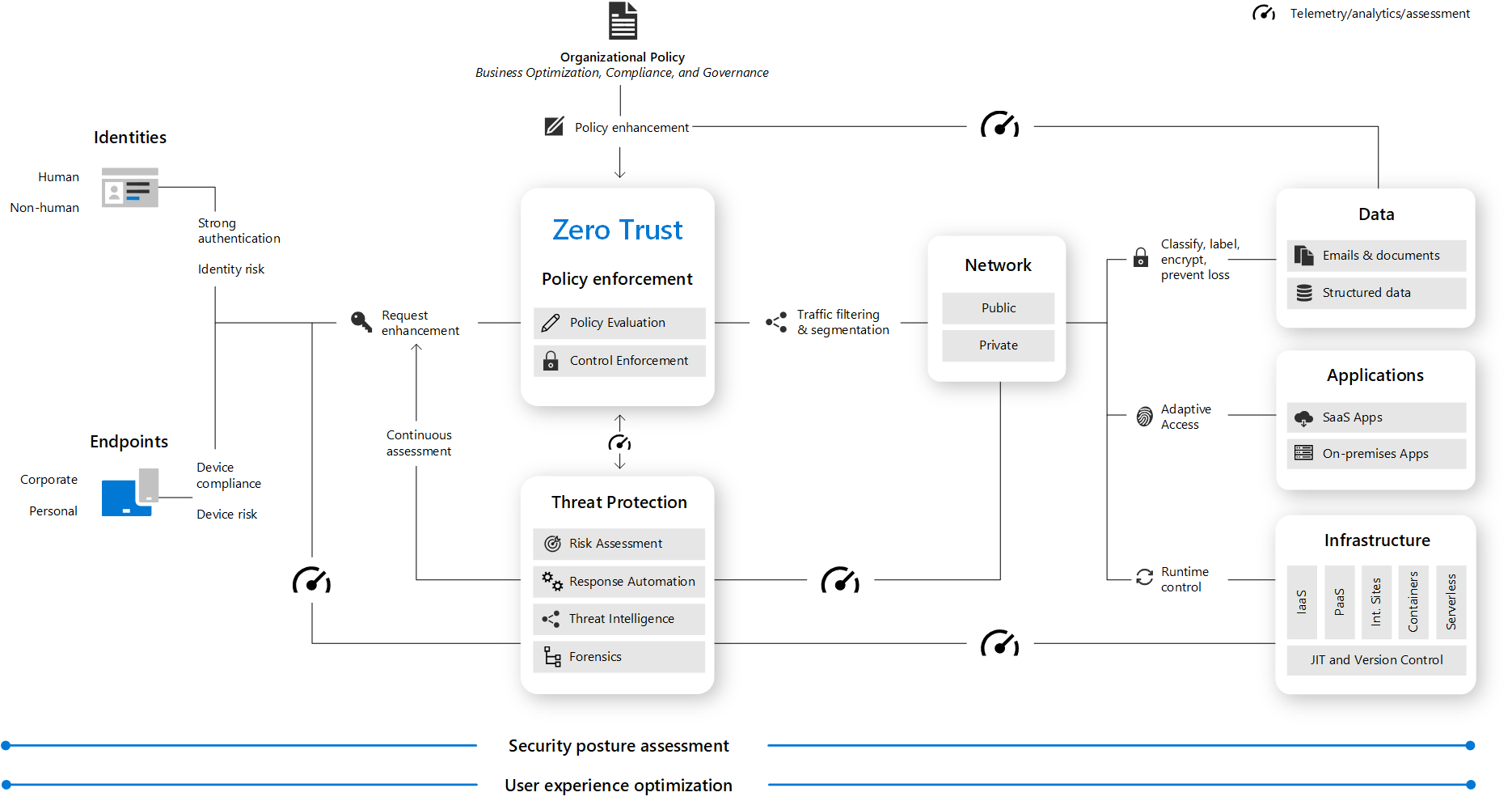
Therefore, this also reflects different architectures, in regards of cloud security, identity and access management, Information protection and governance, risk management, secure remote work, SIEM, and XDR. Certainly, we can spend a lot of time, just on overview of the architecture, as well as the deep dive on each component individually.
Getting around admin portals
Getting into the tooling administrative portals, can get sometimes a little bit crazy. In other words, since last year, Microsoft started unifying the naming convention under the “Defender for” branding :). This made things slightly easier, there is work to be done, and we are getting there.
However, certain portals are not specifically for managing security, they support various workloads and/or tasks that can impact your environment security. Trough these portals we manage identities, permissions, device settings, and data handling policies.
| Portal name | Description | Link |
|---|---|---|
| Azure portal | View and manage all your Azure resources | portal.azure.com |
| Azure Active Directory portal | View and manage Azure Active Directory | aad.portal.azure.com |
| Microsoft 365 compliance center | Manage data handling policies and ensure compliance with regulations | compliance.microsoft.com |
| Microsoft 365 admin center | Configure Microsoft 365 services; manage roles, licenses, and track updates to your Microsoft 365 services | admin.microsoft.com |
| Microsoft Endpoint Manager admin center | Use Microsoft Endpoint Manager to manage and secure devices using combined Intune and Configuration Manager capabilities | devicemanagement.microsoft.com |
| Microsoft Intune portal | Use Microsoft Intune to deploy device policies and monitor devices for compliance | endpoint.microsoft.com |
Getting around security portals
Security operators and administrators can go to the dedicated portals to manage security-specific settings, investigate possible threat activities, respond to active threats, and collaborate with IT admins to remediate issues.
| Portal name | Description | Link |
|---|---|---|
| Microsoft 365 Defender portal | Monitor and respond to threat activity and strengthen security posture across your identities, email, data, endpoints, and apps with Microsoft 365 Defender | security.microsoft.com |
| Microsoft Defender Security Center | Monitor and respond to threat activity on your endpoints using capabilities provided with Microsoft Defender for Endpoint | securitycenter.windows.com |
| Security & Compliance Center | Manage Exchange Online Protection and Microsoft Defender for Office 365 to protect your email and collaboration services, and ensure compliance to various data-handling regulations | protection.office.com |
| Defender for Cloud portal | Use Microsoft Defender for Cloud to strengthen the security posture of your data centers and your hybrid workloads in the cloud | portal.azure.com/#blade/Microsoft_Azure_Security |
| Microsoft Defender for Identity portal | Identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions using Active Directory signals with Microsoft Defender for Identity | portal.atp.azure.com |
| Defender for Cloud Apps portal | Use Microsoft Defender for Cloud Apps to get rich visibility, control over data travel, and sophisticated analytics to identify and combat cyber threats on cloud services | portal.cloudappsecurity.com |
| Microsoft Security Intelligence portal | Get security intelligence updates for Microsoft Defender for Endpoint, submit samples, and explore the threat encyclopedia | microsoft.com/wdsi |
Most importantly, Microsoft 365 Defender portal is available, its improved, and integrates few services. This new experience brings:
- Microsoft Defender for Office 365 helps organizations secure their enterprise with a set of prevention, detection, investigation and hunting features to protect email, and Office 365 resources.
- Microsoft Defender for Endpoint delivers preventative protection, post-breach detection, automated investigation, and response for devices in your organization.
- Microsoft 365 Defender is part of Microsoft’s Extended Detection and Response (XDR) solution that leverages the Microsoft 365 security portfolio to automatically analyze threat data across domains, and build a picture of an attack on a single dashboard.
- Microsoft Defender for Cloud Apps is a comprehensive cross SaaS and PaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
Some more …
Keep in mind, that access to some of the portals or features, requires license to access them. Any of these licenses gives you access to Microsoft 365 Defender features via the Microsoft 365 Defender portal without additional cost:
- Microsoft 365 E5 or A5
- Microsoft 365 E3 with the Microsoft 365 E5 Security add-on
- Microsoft 365 E3 with the Enterprise Mobility + Security E5 add-on
- Microsoft 365 A3 with the Microsoft 365 A5 Security add-on
- Windows 10 Enterprise E5 or A5
- Windows 11 Enterprise E5 or A5
- Enterprise Mobility + Security (EMS) E5 or A5
- Office 365 E5 or A5
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Defender for Office 365 (Plan 2)
If not sure what You have, go to Billing, and review what you have in Licenses section in the Microsoft 365 admin center (admin.microsoft.com).
If You are interested to learn more, check the Detect and respond to cyber attacks with Microsoft 365 Defender learning path, as well as Security Engineer learning and certification options.



Be the first to comment